Grow revenue everywhere with Commerce Cloud.
Scale commerce with confidence on the most complete platform, powered by Einstein 1 — the #1 AI CRM and trusted platform for your customer data. Natively connect your commerce experiences to the #1 sales, service, and marketing apps, and activate data from any source with ease. From fast storefront setup to boosting sales, enhance your ecommerce journey across every customer touchpoint.


Here’s what sets Commerce Cloud apart.




* Salesforce Commerce Platform Metrics; ** Salesforce Commerce Platform Metrics; *** Salesforce 2022 Cyber Week Metrics; **** Salesforce Customer Success Metrics 2022
Fuel growth with AI guidance, from storefront setup to conversions.
Achieve business goals fast with AI-driven actions.
Digital Storefronts
Select the ideal digital storefront for your business objectives with your choice of digital storefront templates, fully headless commerce, or a hybrid approach.
Commerce AI for Merchants
Give your teams the power of conversational AI in their workflows, making it easy to handle any kind of task — from storefront setup to growth.
Commerce Intelligence, Powered by Data Cloud
Save time and optimize every aspect of your business with advanced merchant dashboards and AI insights.
Personalize at scale with AI and real-time data.
Commerce AI for Customers
Elevate online shopping with conversational AI and first party data, mirroring the best in-store interactions across all digital channels.
Customer Acquisition and Loyalty
Earn lasting loyalty by delivering personalized experiences wherever your customers choose to connect - from WhatsApp to the metaverse.
Unlock revenue at every touchpoint on the #1 AI CRM.
Embedded Commerce Apps for CRM
Grow revenue at every step of the customer journey by integrating digital commerce into your sales, service, and marketing channels.
Order Management
Simplify distributed order management for smooth, transparent deliveries and 5-star service.
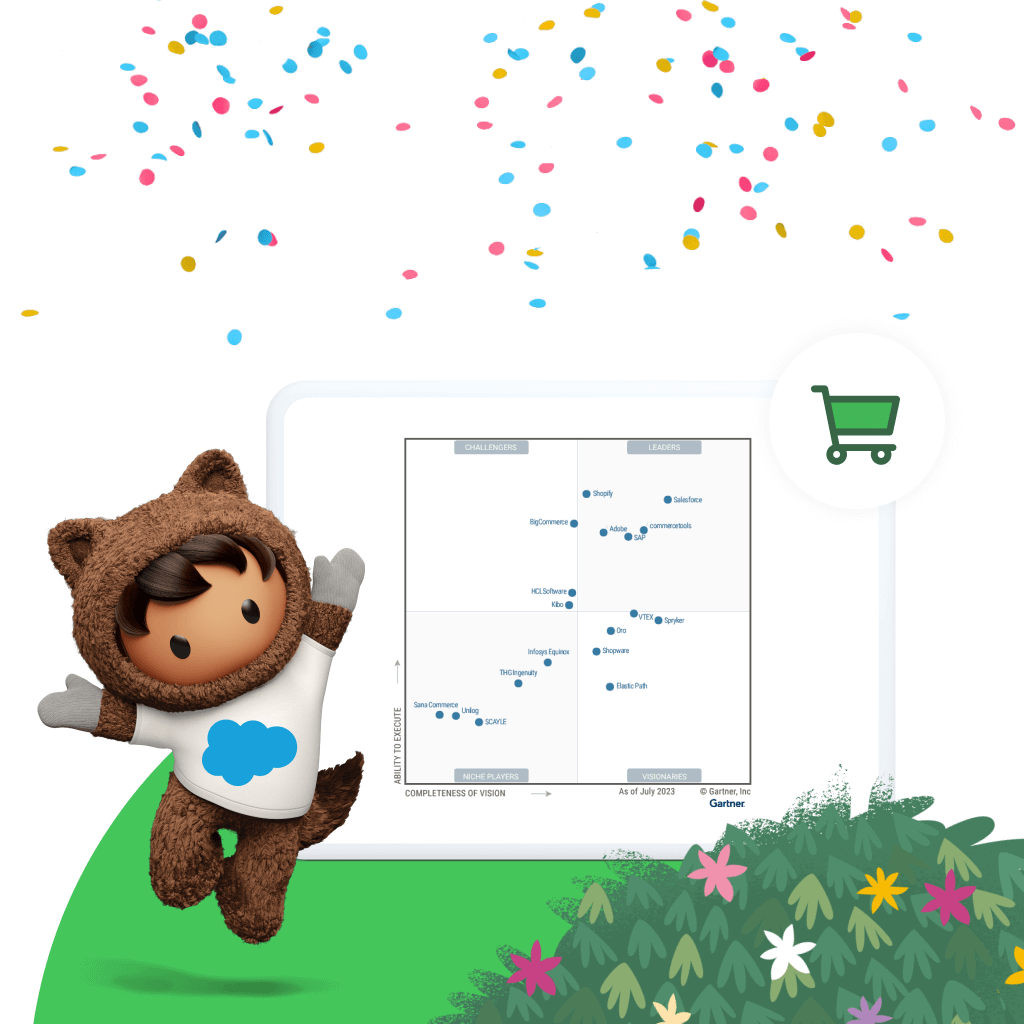
Eight years running, Salesforce is a Leader in the 2023 Gartner® Magic Quadrant™ for Digital Commerce.

Maximize your ROI with the right services for you.
From support, expert guidance, and resources to our trusted partner ecosystem, we’re here to help you get more value from Salesforce in the AI era.

Stay up to date on all things commerce.
Sign up for our monthly commerce newsletter to get the latest research, industry insights, and product news delivered straight to your inbox.
YETI is in a constant state of innovation. We want to be able to do that quickly and Salesforce enables us to do so.
Scott StreitDirector, Software Engineering, YETI
Learn new skills with free, guided learning on Trailhead.
Keep up with the latest commerce trends, insights, and conversations.
Ready to take the next step with Commerce Cloud?
Talk to an expert.
Tell us a bit more so the right person can reach out faster.
Stay up to date.
Get the latest research, industry insights, and product news delivered straight to your inbox.
Salesforce Commerce FAQ
Commerce Cloud is the growth engine for customer companies. Automate sales across the entire customer lifecycle by embedding AI-driven commerce everywhere — from flexible digital storefronts to embedded apps for sales, service, and marketing.
Commerce Cloud helps brands launch sooner, grow faster, and reach more customers. Leveraging the power of the cloud, our trusted technology will help you craft innovative customer experiences that drive higher conversions and average order value (AOV), productivity, and inspire brand loyalty. With artificial intelligence infused into the platform, we enable 1-to-1 personalization without the need for data scientists. Our robust technology partner ecosystem and our team of industry experts ensure your growth from planning to launch, and beyond.
Commerce Cloud includes everything you need for a complete unified commerce experience including digital storefronts, customer acquisition and loyalty tools, reporting and insights, order management, payments, and embedded apps.
In 2016 Salesforce completed the acquisition of Demandware which is now a part of Commerce Cloud.
An ecommerce platform will help you seamlessly launch and grow your digital business through a prebuilt infrastructure. This allows you to reach new customers, reduce operational costs, and grow sales with scalable tools for your online business.
Today's connected customer has high expectations. They interact with retail brands through many touchpoints — web, mobile, social, marketplaces, store, ads, and connected devices — and they want to buy in the moment, at any of these touchpoints. They expect each interaction to run smoothly, and for all interactions to be coordinated into a single, unified experience. Ecommerce software will help you transform your business so you can seamlessly manage online purchases, transactions, inventory, customer data, and create a seamless digital experience for customers.
When choosing the right ecommerce software prioritize a future-proof platform that is trusted, scalable, and readily supports international expansion enabling future growth. Look for a solution architected for flexibility with all the purpose-built tools you need to deliver innovation quickly. It is important to consider the total cost of ownership of any ecommerce solution including ability to integrate with other digital and third-party solutions, uptime, access to advanced features, ongoing support, and implementation.










